Send WEC Events to Azure Sentinel with the Azure Monitor Agent
If you’re using Windows Event Collector (WEC) to centralize your Windows logs and implementing Azure Sentinel, you might be wondering how to get events from the collector to Azure. Using Azure Arc and the new Azure Monitor Agent (AMA), I was able to send the forwarded events to Azure using a custom data collection rule (DCR).
This post assumes that you already have your WEC server and forwarding computers configured, and are familiar with how to onboard servers into Azure Arc.
Background
Azure Arc
Azure Arc is solution that allows administrators to centrally manage their on-premise and non-Azure cloud resources. This includes being able to manage updates with Azure Automation, control governance and compliance standards through Azure Policy, and add advanced threat detection with Azure Defender.
There is no additional cost to onboard servers and Kubernetes cluster to Azure Arc. You do have to pay for the extra features such as policy management, as well as the usual rate for data stored in your log analytics workspace.
Azure Monitor Agent
The Azure Monitor Agent collects monitoring data from systems and sends it to Azure Monitor. The AMA replaces legacy agents, such as the Log Analytics agent. The AMA uses Data Collection Rules to configure data to collect from each agent. In addition to the providing simple checkbox configuration for common data sources, you can create your own data source using an XPath query.
Forwarding WEC Events to Azure Sentinel
Install the Azure Monitor Agent
Installing the Azure Monitor Agent is incredibly easy once you have your server onboarded to Azure Arc. All you have to do is create your first data collection rule, and it’s installed automatically!
Creating a Data Collection Rule
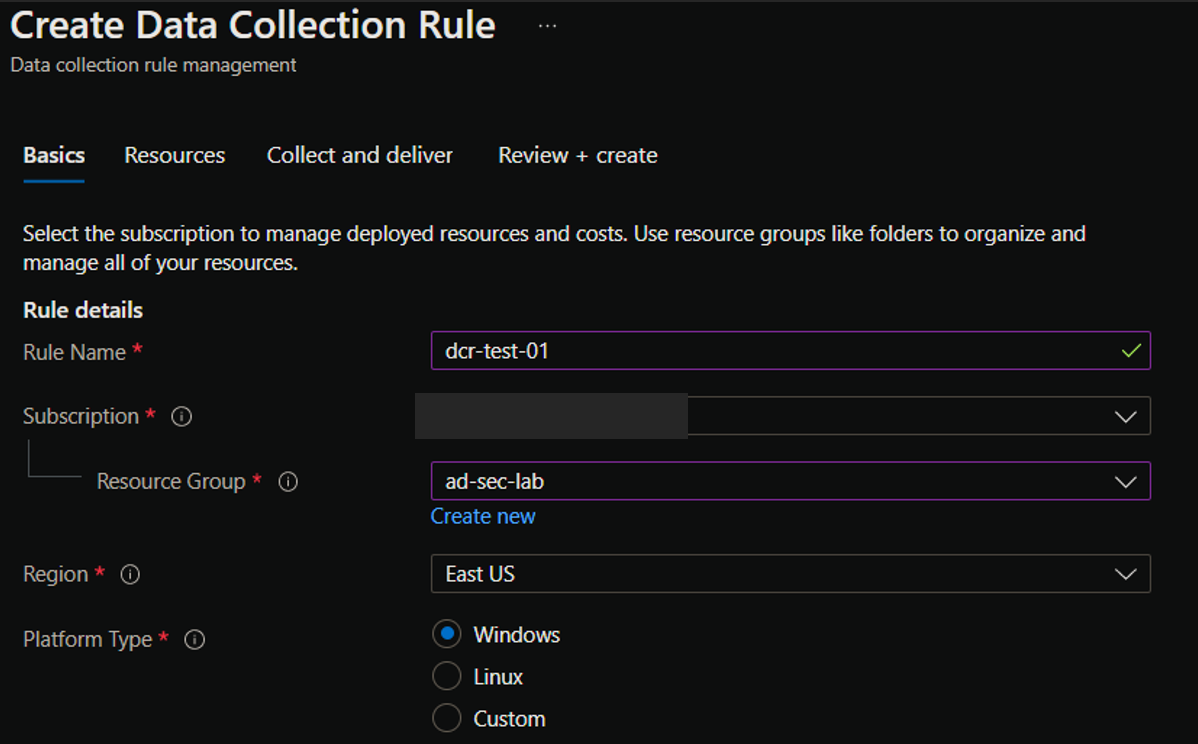
In the Azure portal, navigate to Azure Monitor, then Data Collection Rules under the Settings header. Click Create, and enter in the basic resource information such as the rule name and resource group. Select Windows as the platform type.
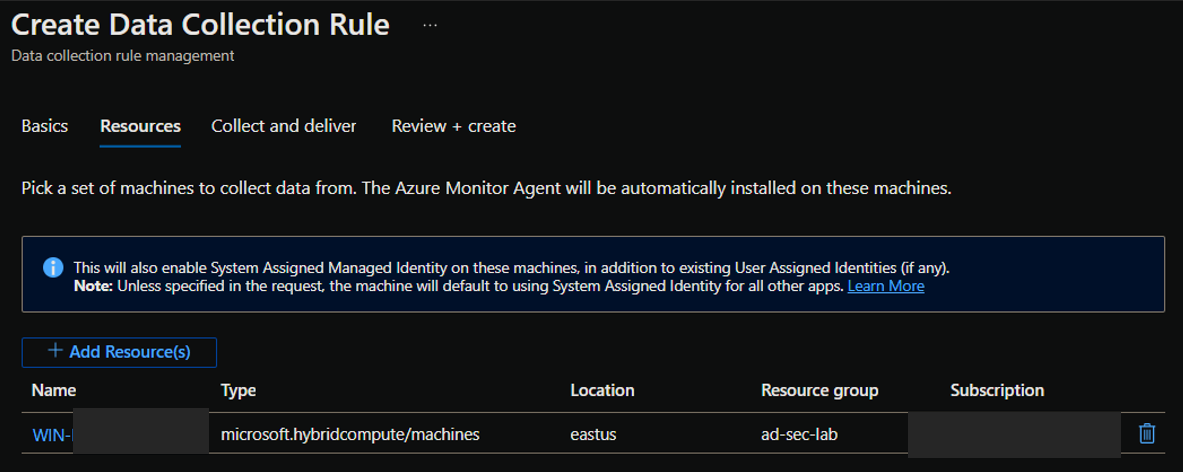
On the next page, you’ll select the resources the DCR applies to. Add your Arc-enabled WEC server.
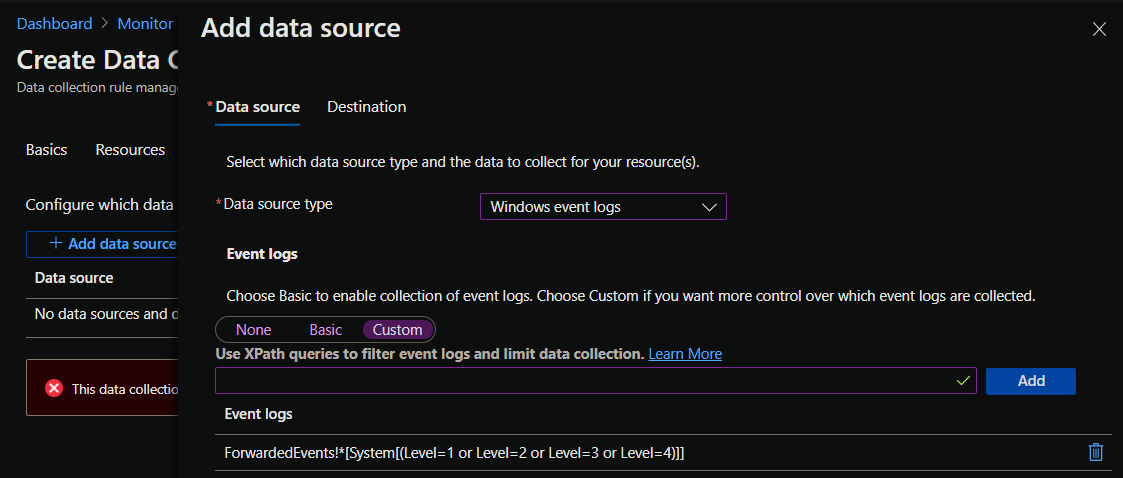
Next, you’ll add the data sources. For data source type, select “Windows event logs”, and select “custom”. In the text field, enter an XPath query to filter the event logs.
Example: Get all events from the ForwardedEvents channel with Informational, Warning, Error, and Critical levels
ForwardedEvents!*[System[(Level=1 or Level=2 or Level=3 or Level=4)]]
After configuring the data sources, you’ll add a destination where the logs will be stored.
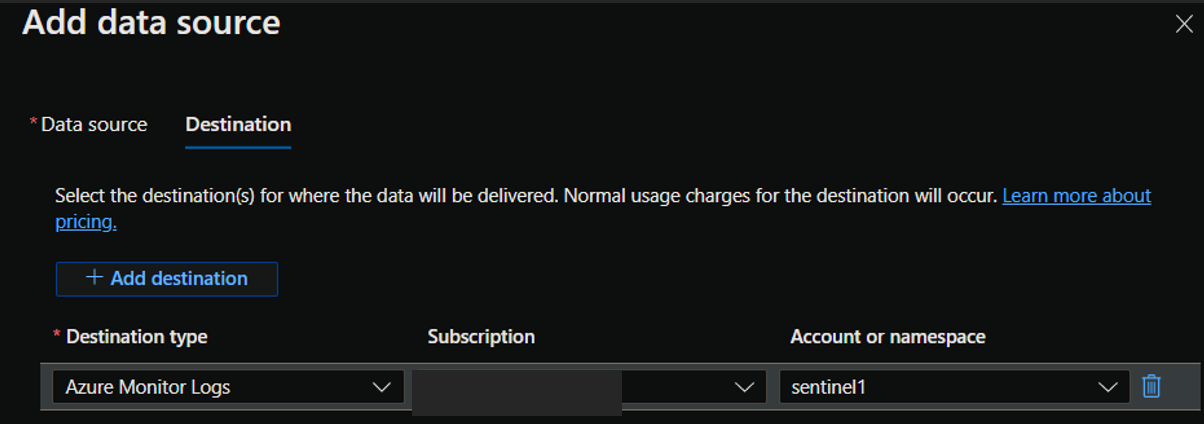
Finally, Review your new rule and ensure validation passes, then click create. Congratulations, you’ve built your first data collection rule!
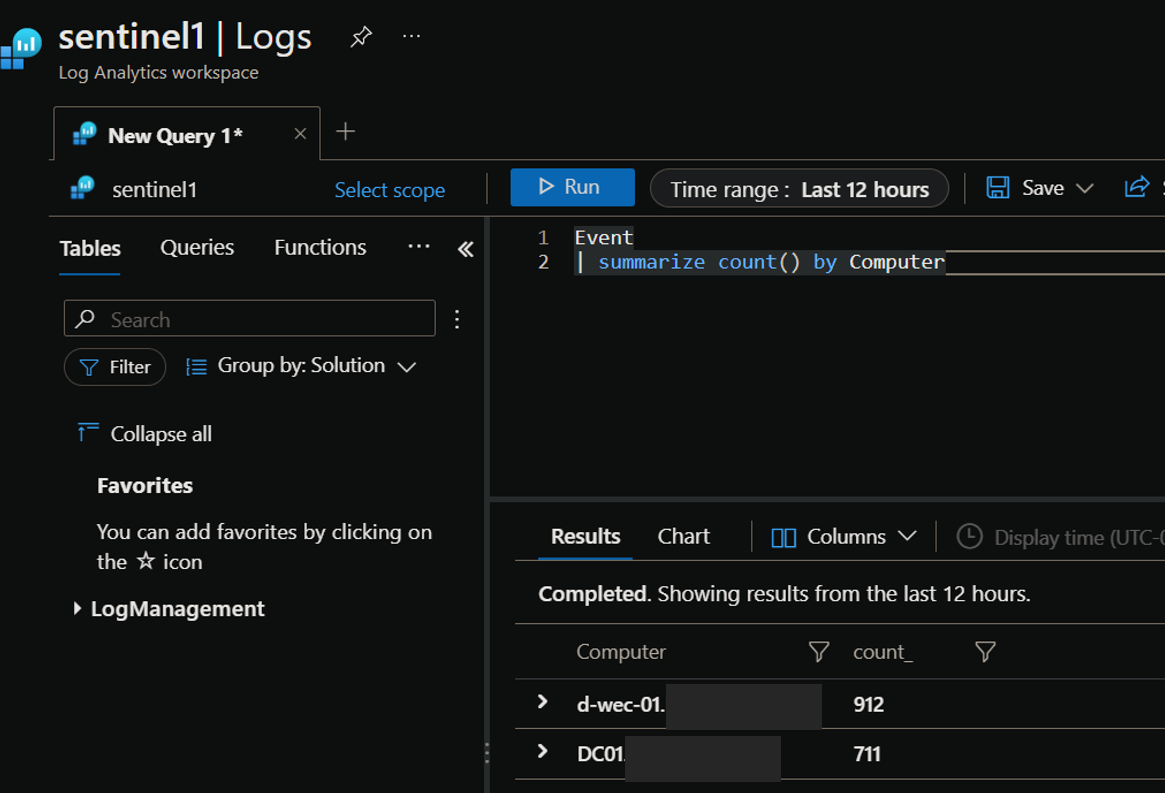
View Logs in Sentinel
After some time, you should start seeing your WEC events flowing into the workspace you set as the destination. In my example, I was sending logs from my domain controller “DC01” to my WEC server “d-wec-01”: