IceCTF 2016 Writeups

Over the past couple of weeks, I participated in an Icelandic capture the flag competition, hosted by IceCTF. The challenges ranged from very easy to quite difficult. I managed to solve about a dozen or so challenges, so this post will be quite long.
Vape Nation - Stego 50pts.
Description: Go Green! vape_nation.png
For this challenge you were given a .png image (seen below).
Image
To find the flag, I used a nifty program called StegSolve. From there, I played around with some of the analysis options until I found the flag using the “Green plane 0” setting.
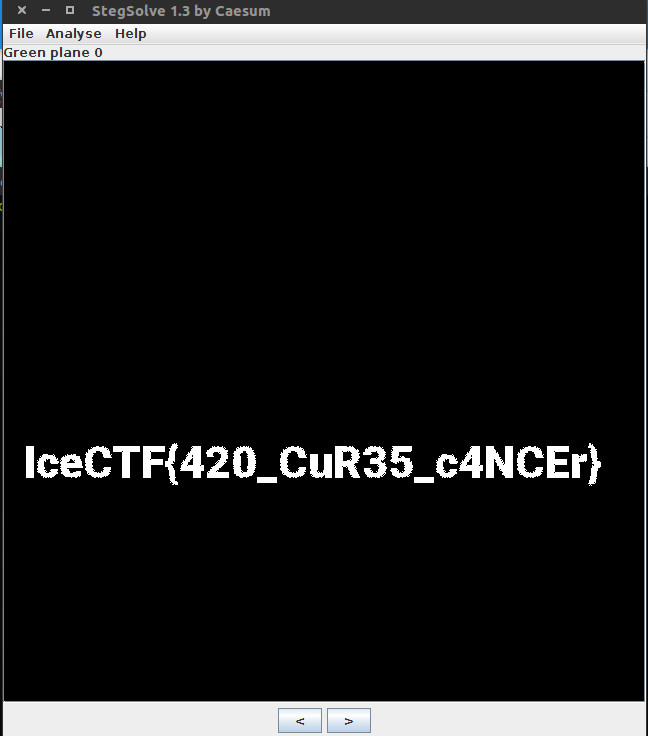
Flag: IceCTF{420_CuR35_c4NCEr}
Corrupt Transmission - Forensics 50pts.
Description: We intercepted this image, but it must have gotten corrupted during the transmission. Can you try and fix it? corrupt.png
Trying to open up the image files results in an error. So, logically we might want to try and see if we can fix this to see what our image is hiding. The first thing I did was open up the file in a hex editor to see what’s going on behind the scenes:
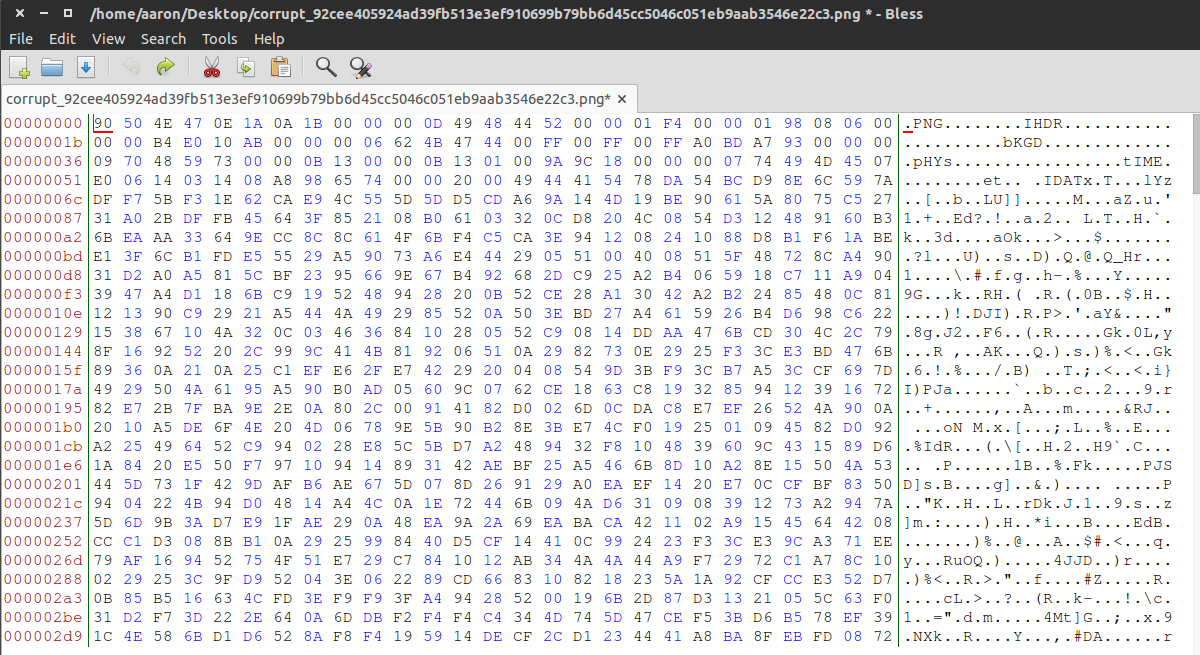
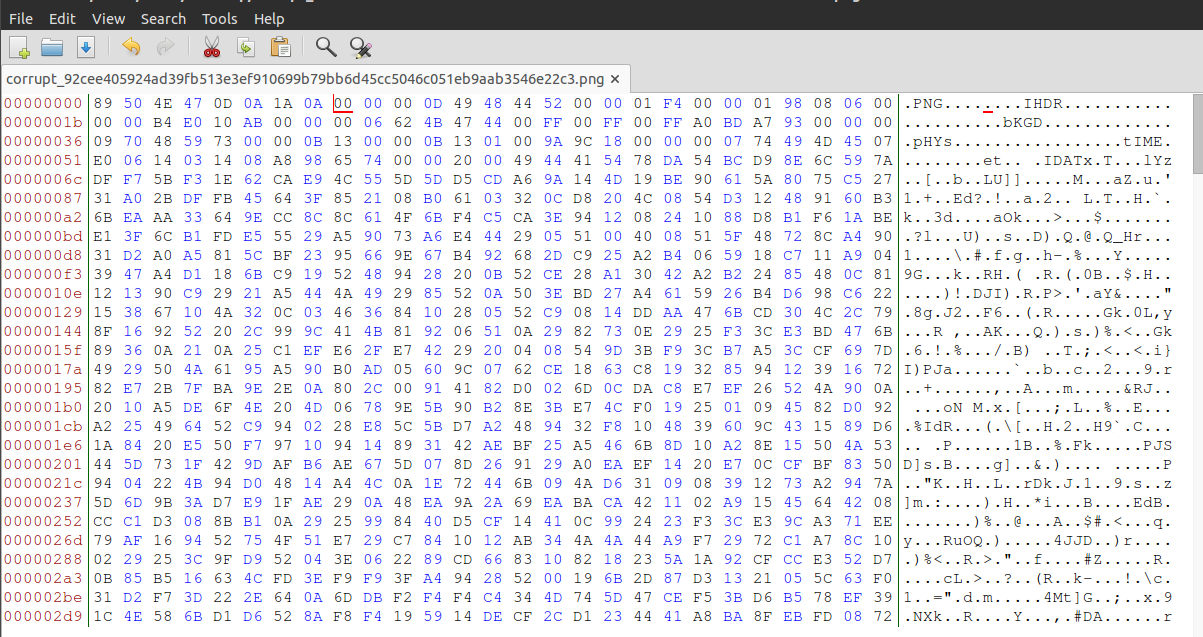
We can see that the first 8 bytes are not the correct PNG signature. I then made the changes to match the correct bytes, and then re-opened in the image viewer to receive the flag:
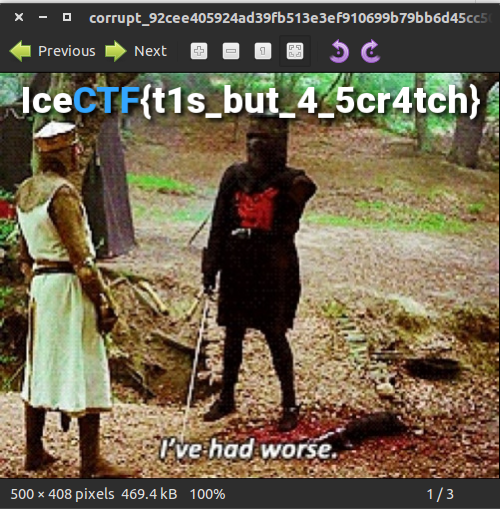
Flag: IceCTF{t1s_but_4_5cr4tch}
Audio Problems - Stego 50pts.
Description: N/A
For this task we are given an audio file. I opened up the file in Audacity, and tried playing the file - no such luck for any recognizable audio. I used the Spectrogram view, to which I can see there’s definitely something hiding within the file’s audio frequencies. After playing with the settings to see if I can get a better visualization, the “Hamming” window type revealed the flag (or, at least as close as I could get it):
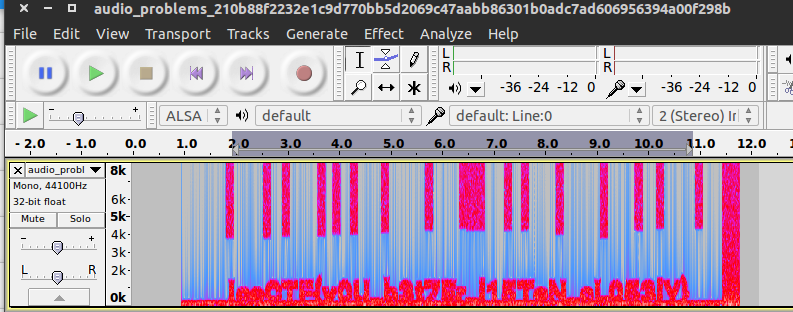
Flag: IceCTF{y0U_b3t7Er_l15TeN_cL053lY}
Flag Storage - Web 50pts.
Description: What a cheat, I was promised a flag and I can’t even log in. Can you get in for me? flagstorage.vuln.icec.tf. They seem to hash their passwords, but I think the problem is somehow related to this.
Navigating to the URL provides us with a login page:
I first check for the obvious things like default administrator credentials, such as admin/admin, root/root, etc. From there, I decided to check and see if this page was vulnerable to SQL injection. Using a basic string ( ’ OR 1=1#; ), I was successfully logged in and given the flag:
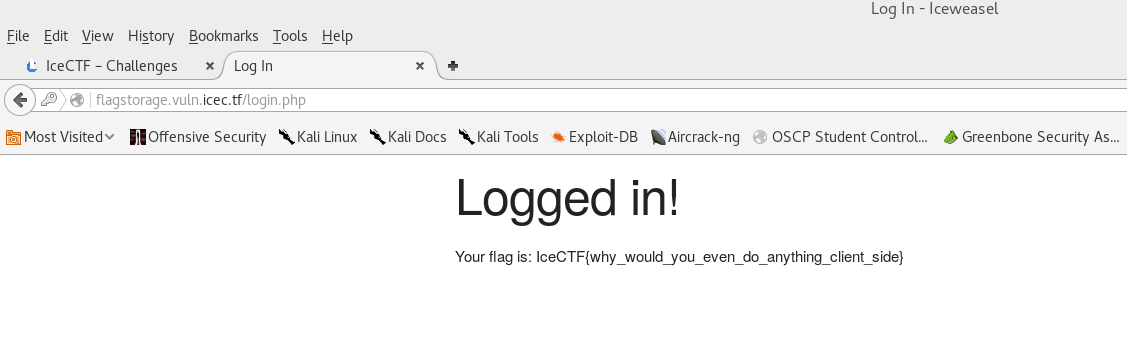
Flag: IceCTF{why_would_you_even_do_anything_client_side}