Trend Micro CTF 2016 Writeups
Misc./IoT - 100 pts.
Description
Category: Misc(iot and network)
Points: 100
Please analyze this pcap.
Decrypt the downloaded file by the following command.
$ unzip files21.zip
$ openssl enc -d -aes-256-cbc -k gcCbBJN5pIHiL8JiJ8Xj -in files21.enc -out files21_ok.zip
$ unzip files21_ok.zip
After opening the file in wireshark, it seems that we are viewing the history of someone interacting with a machine using telnet. They attempt to login using default credentials like admin/admin, and finally succeed using an account called “reds”. They then start to check things like users on the machine, disk space, and network connectivity. Eventually, we get to some ESP packets that were sent along an encrypted tunnel.
After doing some googling on ESP packets, I found a Wireshark forum thread about decrypting ESP packets: https://ask.wireshark.org/questions/12019/how-can-i-decrypt-ikev1-andor-esp-packets
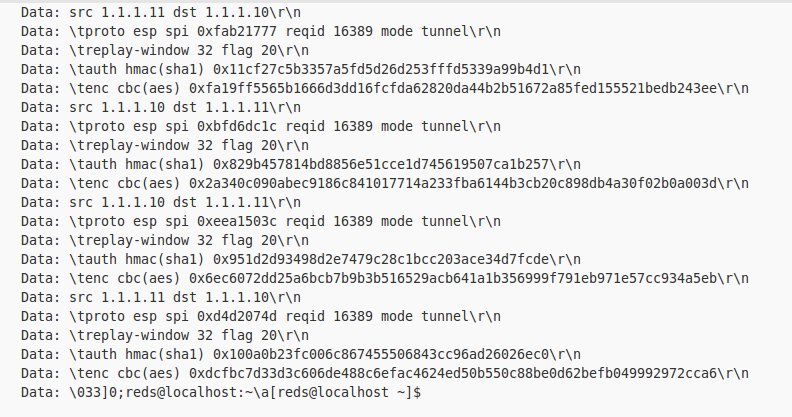
Basically following those exact instructions allowed me to decrypt the packets and see what the attacker was up to. Luckily, there was a packet that showed the encryption/authentication keys in plaintext.
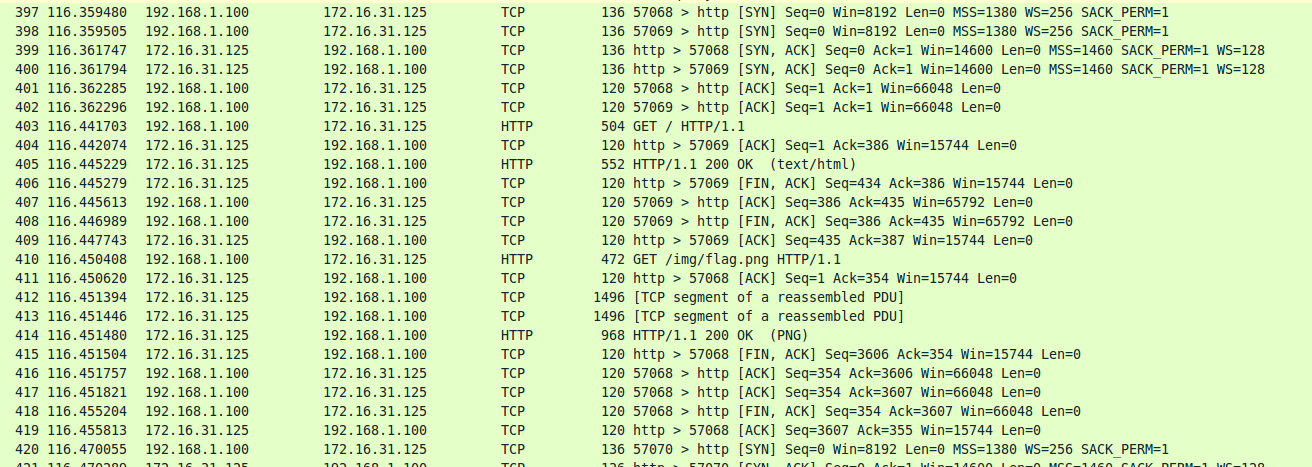
We can see that the results show a few HTTP GET requests, and of particular interest is a request for “/img/flag.png”.
Grabbing that image gives us our flag.
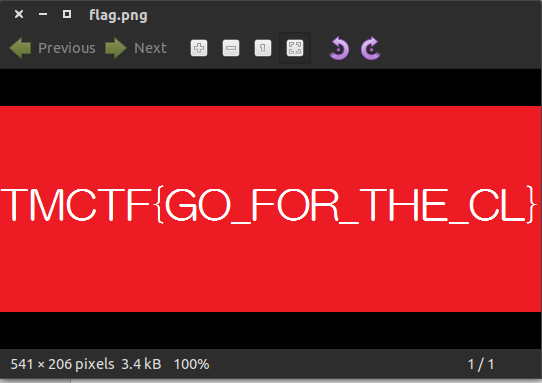
Flag: TMCTF{GO_FOR_THE_CL}